Intelligence
Applied
Powered by AI, built on Microsoft Azure
Drive new growth and multiply opportunities for your firm with the industry cloud designed for professional and financial services.
A proven industry leader
Intapp is a leading global provider of software for more than 2,400 professional and financial services firms.
- 2.4k+
- client firms worldwide
- 96
- of the Am Law 100
- 1.6k+
- private capital and investment banking firms
- 15
- top 20 accounting firms
Top firms trust us.
You can too.
AI-powered solutions for your industry
Move fast, modernize operations, and win more business with Intapp’s tailored cloud-based solutions.
Empower your teams, strengthen your client relationships, and reduce risk
- DealCloud
- Help your teams execute at the highest level with a data-powered platform that’s so much more than just a CRM.
- Compliance
- Quickly and thoroughly evaluate new business, onboard clients, and monitor relationships for compliance.
- Collaboration
- Support modern ways of working, minimize information governance risk, and improve client service delivery.
- Time
- Automate timekeeping, reduce write-offs, maximize realization, and increase client satisfaction.
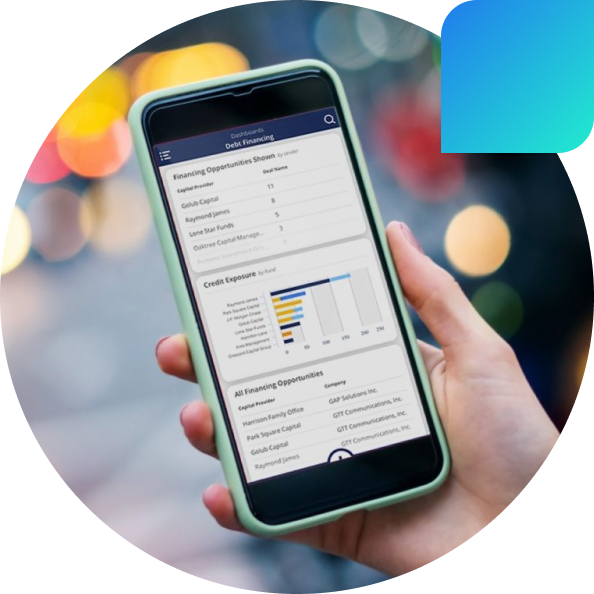
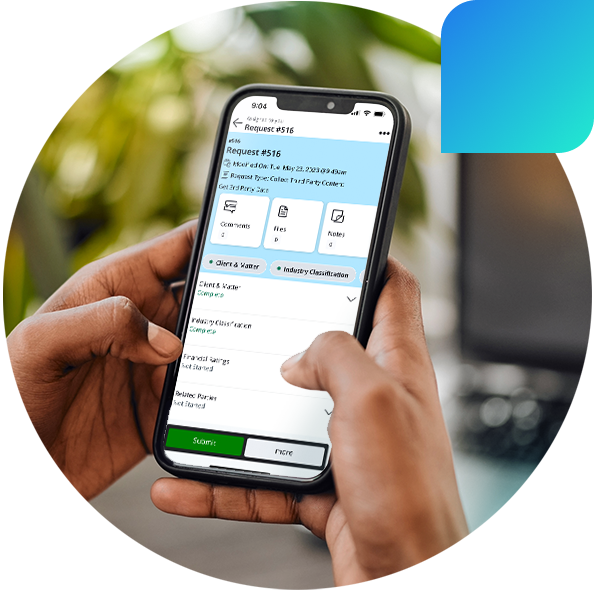

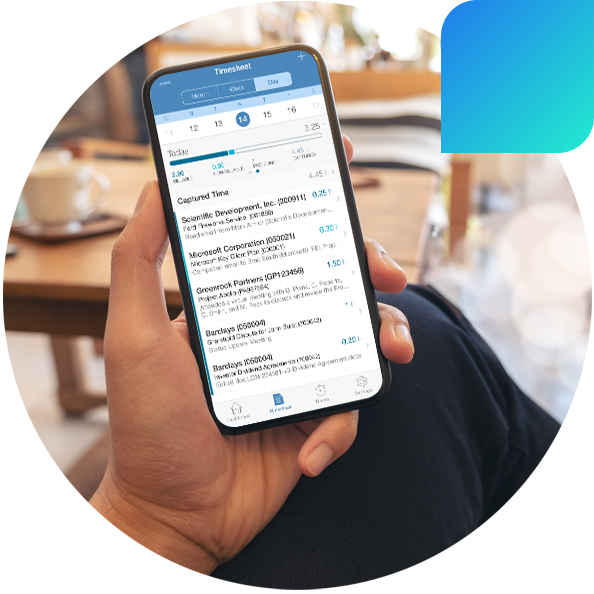
Intapp Intelligent Cloud
For more than a decade, Intapp has been bringing the power of automation and intelligence to professional and financial services firms — helping clients like you solve their specialized needs and challenges.
Intapp Cloud Infrastructure
Use AI confidently, knowing we keep your data secure through our partnership with Microsoft and our own commitment to security and compliance.
Learn more about our cloud infrastructureIntapp Data Architecture
Quality data is at the heart of good AI — and with Intapp, you benefit from our data architecture.
Learn more about our data architectureIntapp Applied AI
Our Applied AI strategy includes five essential AI capabilities that help you make smarter decisions, faster.
Learn more about our Applied AI strategy






